|
<< Click to Display Table of Contents >> Patient Audit Log |
  
|
|
<< Click to Display Table of Contents >> Patient Audit Log |
  
|
The Patient Audit Log will display audit data that occurred after the installation of Version 20. For audit data prior to the Version 20 installation, please see the Patient Audit Log -Data Pre-Version 20. This audit log is used to help protect the electronic health record and to conduct or review a security risk analysis. It is also used to implement security updates as necessary and correct identified security deficiencies as part of its risk management process.
To meet this objective, the facility must be using Linux, UBLs, Encryption, Patient Audit Log and Break the Glass functionality, which is supported by Point of Care.
NOTE: In order to preserve disk space, Patient Audit Log data older than three months will be compressed and archived by TruBridge. If needing to view data older than three months, please contact TruBridge Technical Support to uncompress and restore the data.
Select Web Client > Report Dashboard > Patient Audit Log
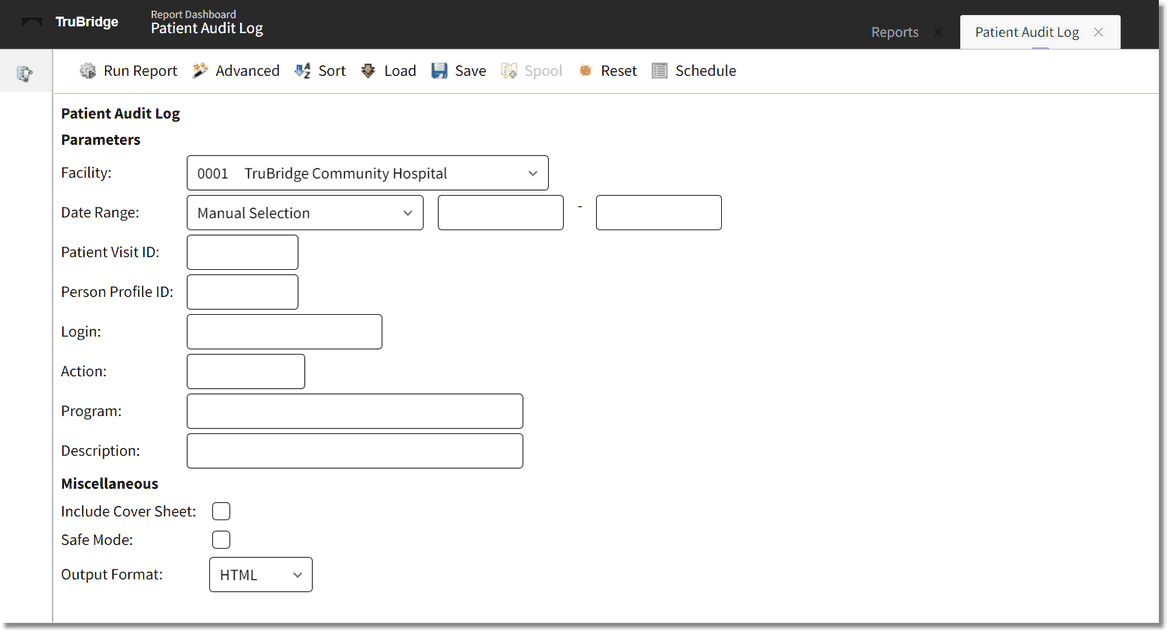
Patient Audit Log Parameters
•Facility: Select the desired facility to view audit information.
•Date Range: Use the drop-down box to select a date, or choose Manual Selection to enter a date manually. When the date is entered as MMDDYY, the system will automatically change it to MMDDCCYY format. A date range must be specified in order to run the report.
•Patient Visit ID: Enter the desired patient account number to pull to the Patient Log.
•Person Profile ID: Enter a specific person profile number to be audited. When searching by person profile number, the results will display actions that occurred on the profile and all visits attached to the profile. The Person Profile Number is displayed in the upper right-hand corner of the profile. Leave this field blank to run for all profiles.
•Login: Enter the employee or physician login to be audited. The ability to wildcard the login is available using an asterisk (*). For example, entering john* will find results for john, johna, johnb and john12. This makes it easier to audit users that have multiple logins.
•Action: Enter an action to be audited or leave blank for all actions.
•Program Name: Enter the program name (launcher name) to see audit data for that program name only. If this field is left blank, the report will run for all program names.
•Description: Enter the description of the table to be audited. Leave this field blank for all tables.
•Include Cover Sheet: Select this option to have a cover sheet pull with the Date and Time the report was run, User, Facility, Date Range of report and Section.
•Safe Mode: Select this option if the report would not build due to bad data being in a field. If the report has bad data, a message will appear stating to run report using the Safe Mode. If selected, Safe Mode will replace all of the bad characters with a ?. This will allow the intended report to generate. The bad data may then be seen and may be corrected from the account level.
•Output Format: Use the drop-down box to select one of the following report Format options:
▪HTML
▪XML
▪CSV
▪MAPLIST
▪TXT
Patient Audit Log
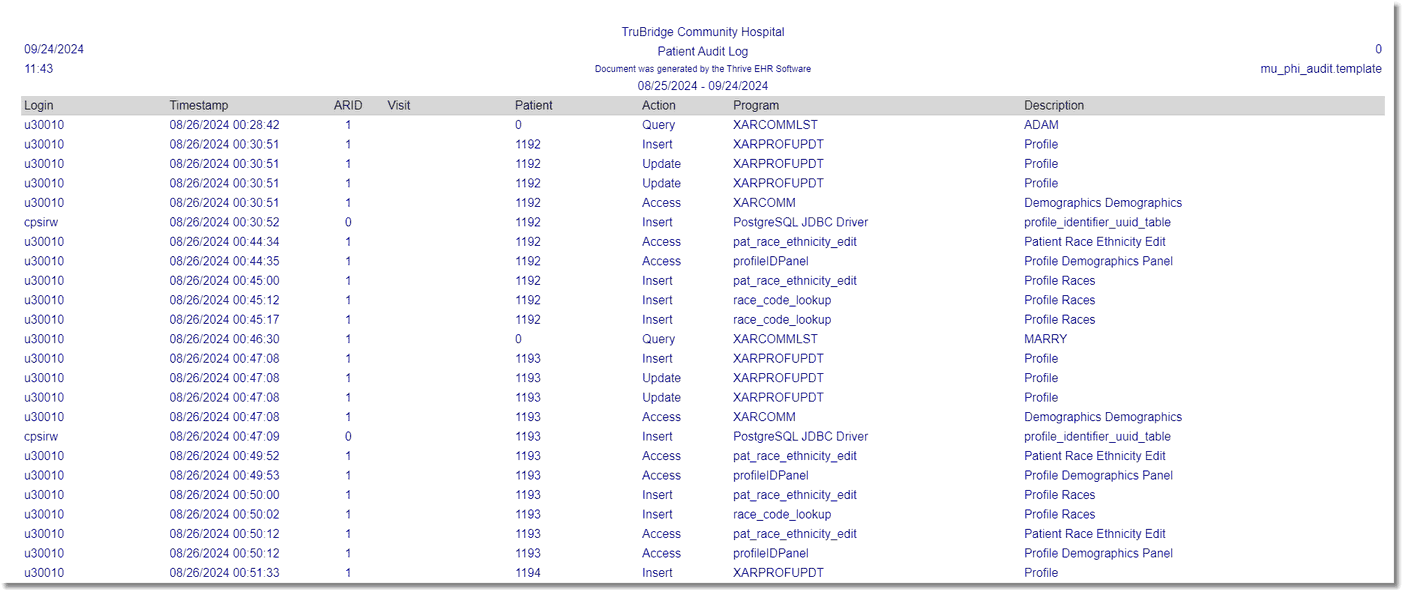
Patient Audit Log Report
Listed below is an explanation of each column.
•Login: Pulls the employee or physician login.
•Timestamp: Pulls the date and time (hour, minute and seconds) that a transaction occurred.
•ARID (Accounts Receivable ID): Pulls the Accounts Receivable ID number that is associated with the facility in the Facility table.
•Visit: Pulls the Patient Account Number where the action occurred.
•Patient: Pulls the Person Profile Number where the action occurred. The Person Profile Number is displayed in the upper right-hand corner of the profile.
•Action: Pulls one of the following actions that occurred.
▪Query: A search by Patient Name was performed within Thrive. The Description displays the search criteria that was entered in the patient name lookup.
▪Access: An area of Thrive was viewed but not updated. .
▪Insert: A database transaction where a new record is created in a table.
▪Update: A database transaction where an existing record is modified in a database table..
▪Delete: A database transaction where an existing record is permanently deleted from the database table.
▪Print: An EHI element was printed or viewed in a PDF©.
▪Copy: A copy of an EHI element was exported for use outside the Thrive EHR.
▪FHIR Copy: A copy of an EHI element was exported for use outside the Thrive EHR thru API capabilities.
▪Auth Query: There was a successful attempt to acquire a Token given to a third party application to access PHI. The third party application is set up with credentials (login and password) to access PHI via the Patient Portal Login that is in the Login field on the report.
•Program: Pulls the program name or launcher name associated with the action.
•Description: For Insert, Update and Delete actions the description will display the database table that was affected by the action. For Query actions, the description will be the name that was entered in the patient name lookup. For Print and Copy actions the description will be the name of the report or document that was accessed.
NOTE: Entries in the Patient Audit Log can only be made by successfully authenticated users authorized by the facility to access electronic health information stored in Thrive. Mechanisms and triggers have been designed to detect if the Audit Log has been accessed, modified or otherwise tampered with from outside Thrive. When a tampering event has been detected, notifications are sent to TruBridge via Remote Communications, and sites will be informed regarding the status of the audit log. For more information regarding this, please contact TruBridge Software Support.
NOTE: The Report Scheduler may also be used with the Patient Audit Log report. For more information please refer to the Report Scheduler section of the Report Dashboard user guide.