|
<< Click to Display Table of Contents >> Security Change Log |
  
|
|
<< Click to Display Table of Contents >> Security Change Log |
  
|
The Security Change Log displays the changes made during an auditable event. Changes may only be viewed on the following actions: Insert, Update, and Delete. In addition, the database table associated with the field that was changed must have the audit level set to Change Level in order to view change information. The Security Change Log may be accessed from the System Administration menu or from within the Security Audit Log.
Select Web Client > System Administration > Security Change Log
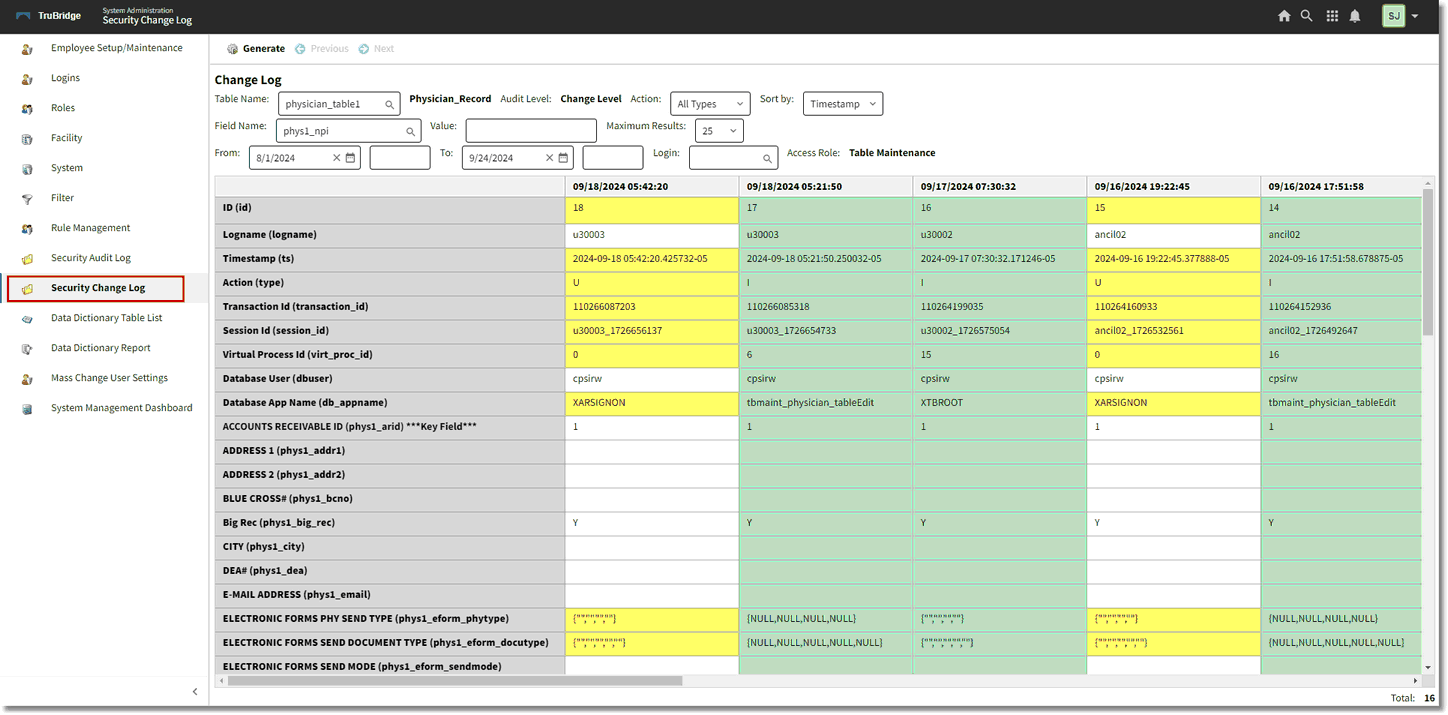
Security Change Log
The information that displays in the audit log may be delimited using the following options:
•Table Name: Enter the database table name to be audited. The table name must be selected to search for Change Log information.
•Audit Level: This field will display the audit level for the selected table.
•Action: Select an action to be audited from the drop-down list or leave blank for all actions.
•Sort by: Select a field to sort the audit data by from the drop-down menu.
•Field Name: Select a field from the selected table to search for a specific value in that field.
•Value: The Value field works with the Field Name option. Select a Field Name to search by and then enter the corresponding search criteria in the Value field.
•Maximum Results: Select the maximum number of results that should display.
•From/To: This is the date/time range to be audited.
•Login: Enter the employee or physician login to be audited. The ability to wildcard the login is available using an asterisk (*). For example, entering john* will find results for john, johna, johnb and john12. This makes it easier to audit users that have multiple logins.
•Access Role: This is the Database Access Role assigned to the table. This may be used to identify the Audit Access Behavior Control that is needed in order to view the change information for the selected table. For example, if Accounts Receivable is displayed, the user will need the Behavior Control for Audit Access for Accounts Receivable Role set to allow. This is also the Database Access Role assigned to the table.
NOTE: If accessing the Security Change Log from the Security Audit Log, the parameters above will automatically be populated.
The following data is displayed with each audit entry.
•Id: This is the table sequence number. Each change to a database table will be assigned a sequence number. All table changes will display in reverse chronological order, so the most recent change displays in the first column and the oldest change displays in the last column.
•Logname: Pulls the employee or physician login.
•Timestamp: Pulls the date and time (hour, minute and seconds) that a transaction occurred.
•Action: Pulls one of the following actions that occurred.
•I (Insert): A database transaction where a new record is created in a table. These changes will be highlighted in Green.
•U (Update): A database transaction where an existing record is modified in a database table..These changes will be highlighted in Yellow.
•D (Delete): A database transaction where an existing record is permanently deleted from the database table. These changes will be highlighted in Red.
•Transaction ID: This is a unique identifier given to every transaction operation (insert, update, delete) executed at the database table level. Understand that some options such as a “Save or Edit or Update” option in the end user application can result in multiple transactions across several tables. This identifier ties all those transactions together to indicate all occurred via the same option.
•Session ID: A unique identifier assigned to each user at the time of login and remains with the user until he/she logs out. The purpose of the Session ID is to make it easier to trace through an auditing scenario.
•Virtual Process ID: The Virtual ID Process assists TruBridge Support in troubleshooting error messages and problems.
•Database User: This is the database entry point.
•Database App Name: Pulls the program name or launcher name associated with the action.
Below the Database App Name, the fields that belong to the table that was changed will display. Fields will be listed in alphabetical order. The fields that have been changed will be highlighted in either Green, Yellow, or Red depending on the type of action that occurred.
Color |
Action |
Green |
Insert |
Yellow |
Update |
Red |
Delete |